The amount of cyber strikes and information violations in recent years is astonishing as well as it's very easy to produce a shopping list of companies that are family names that have been impacted. Below are simply a few instances. For the full listing, see our biggest information violations post. The Equifax cybercrime identity theft occasion impacted approximately 145.
In this instance, protection concerns and answers were also compromised, increasing the risk of identification theft. The breach was initially reported by Yahoo on December 14, 2016, and compelled all impacted individuals to transform passwords as well as to reenter any unencrypted security inquiries as well as solution to make them encrypted in the future.
The Greatest Guide To Cyber Security Company

Cybersecurity is comparable to a bar or a club that weaves with each other lots of steps to protect itself and also its clients. The most typical spyware usually records all customer task in the device where it is installed. This leads to assailants figuring out sensitive information such as credit scores card information.

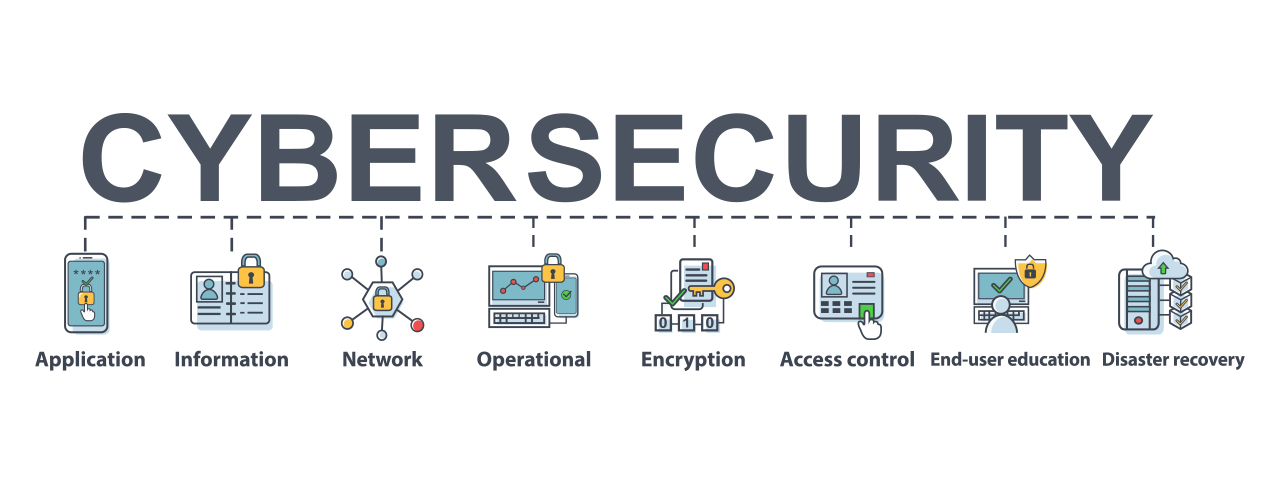
Cybersecurity is a big umbrella that covers different security components. It is very easy to get overwhelmed and also shed focus on the large picture. Here are the top 10 finest methods to comply with to make cybersecurity initiatives more effective. A cybersecurity strategy should start with recognizing all elements of the framework as well as individuals who have accessibility to them.
3 Easy Facts About Cyber Security Company Explained
This is either done by internet services exposed by each service or by making it possible for logs to be readable among them. These remedies should be able to grow in tandem with the company and with each various other. Losing track of the most recent safety and security patches as well as updates is simple with multiple security solutions, applications, systems, and also gadgets involved - Cyber Security Company.
The more essential the source being safeguarded, the extra frequent the update cycle requires to be. Update plans have to belong to the preliminary cybersecurity strategy. Cloud framework and nimble methodology of working guarantee a continuous development cycle (Cyber Security Company). This implies brand-new sources and also applications are contributed to the system everyday.
The Single Strategy To Use For Cyber Security Company
The National Cyber Protection Partnership recommends click to find out more a top-down technique to cybersecurity, with corporate administration leading the fee throughout business procedures. By integrating input from stakeholders at every degree, more bases will certainly be covered. Even with one of the most sophisticated cybersecurity tech in area, the onus of safety and security usually drops on the end individual.
An educated worker base has a tendency to boost security pose at every degree. It appears that despite the market or size of a service, cybersecurity is a developing, crucial, and non-negotiable process that expands with any kind of firm. To make certain that cybersecurity initiatives are heading in the right instructions, many nations have governing bodies (National Cyber Safety And Security Centre for the U.K., NIST for the united state, and so on), which provide cybersecurity standards.
Not known Facts About Cyber Security Company
We performed a study to better comprehend how boards deal with cybersecurity. We asked directors just how usually cybersecurity was talked about by the board as well as found that just 68% of participants claimed frequently or continuously.
When it pertains to comprehending the board's duty, there were numerous alternatives. While 50% of respondents claimed there had actually been discussion of the board's duty, there was no agreement concerning what that function must be. Giving guidance to operating managers or C-level leaders was seen as the board's role by 41% of participants, taking part in a tabletop workout (TTX) was mentioned by 14% of the respondents, as well as basic recognition or "on call to published here respond needs to the board be needed" was stated by 23% of Directors.
Cyber Security Company Fundamentals Explained
It's the figure's function to make sure the company has a plan and also is as prepared as it can be. It's not the board's duty to compose the plan. There are several structures offered to help a company with their image source cybersecurity approach. We like the NIST Cybersecurity Framework, which is a structure established by the U.S
It is straightforward as well as provides execs and also directors a great framework for thinking with the important elements of cybersecurity. It likewise has several levels of information that cyber professionals can make use of to install controls, processes, as well as procedures. Effective application of NIST can prepare a company for a cyberattack, and also reduce the adverse after-effects when an assault occurs.
The Best Guide To Cyber Security Company